In December 2020, the SolarWinds “Orion” attack resulted in more than 18,000 customers unwittingly installing malicious code as part of a run-of-the-mill software update, compromising global companies’ critical supply chains and costing cyber insurance firms upwards of $90 million. Similarly, the recent Coronavirus disease (COVID-19) Vaccine Cold Chain Global Phishing campaign was a cyberattack against the key organizations running the COVID-19 cold chain. These phishing attacks tried to gain credentials for accessing sensitive information about the vaccine distribution, which in all likelihood, led to significant information leaks.
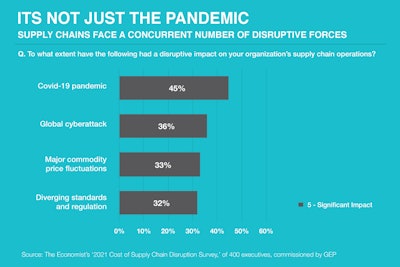
According to The Economist’s recent survey of 400 executives at U.S. and European companies, more than one-third (36%) reported cyberattacks “significantly” disrupted their supply chains in the last three years. In fact, cyberattacks were second only to COVID-19 as the force wreaking havoc with the world’s supply chains in 2020. With an average cyberattack costing approximately $3.9 million due to system downtime, damaged reputation, lost business or other factors, it is imperative that we bolster efforts to secure our supply chains.
The first thing to understand is that the number of security breaches is directly proportional to the level of supply chain automation. Specifically, the improper implementation of automation is what increases the susceptibility of a supply chain. So, breaches will grow exponentially as we hurriedly move toward a fully automated supply chain, with statistics projecting damages directly driven by cybercrimes to reach $6 trillion by the end of this year.
 GEP
GEP
Here are steps you can take to protect supply chains from cyberattacks.
1. Identifying where the risk lies. The most common causes of supply chain breaches are weak and stolen credentials, application vulnerabilities, malware, excess permissions, insider threats and user error. So, conduct a thorough evaluation of your supply chain partners and understand what data is being shared with whom. Ensure maximum security and limit your data exposure by establishing where unnecessary data is being shared. Minimize access to cloud servers storing important information.
2. Secure supplier contracts. Instead of thinking about security after completing contract negotiation, incorporate it into the contract from the very start and be clear about what information is required and by whom. Ensure only limited access to third-party vendors (with third-party vendor misuse being one of the biggest security threats today).
3. Conduct vulnerability mitigation and testing. By running vulnerability scans, you can identify various security concerns such as poor password choices or bad database configurations and mitigate the level of risk for various fragments of the supply chain.
4. Encrypt data. All protected customer information should be contained in encrypted and secure files that are constantly updated to keep pace with the newest technologies.
5. Establish incident response protocols. While supply chains should mitigate the risks of security breaches, you must be ready to respond to such incidents by having a plan in place. By preparing a handy template to record all key aspects of an incident to ensure consistency, readily available forensic imaging tools and the contact details of all key stakeholders to ensure quick outreach, you can minimize the damage from an attack.
Supply chain attacks will continue to increase costs and in propensity. In fact, the greatest threat to supply chains going forward is not pandemics, trade wars or tariffs; it’s cyberattacks. While we automate our supply chains, we must simultaneously harden our security to protect, track and respond.