A growing number of organizations are being exposed to IT disruptions that can impact systems supporting day-to-day operations. The risk presented by IT disruptions is an urgent priority for leaders given the technology necessary to support complex global supply chains; however, it is evident that many organizations’ risk management processes are insufficient to the task at hand. The American Productivity and Quality Center (APQC) recently conducted research to examine the current state of IT risk in the supply chain. The research revealed that organizations occasionally use IT risk management practices and that they find these practices to be only somewhat effective. These findings highlight the need for organizations to adopt risk management practices that align with corporate strategy and are visible within the enterprise.
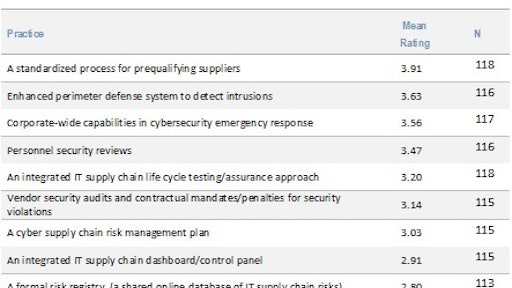
Survey respondents indicated how often their organizations use certain practices to manage the IT risk in their supply chains. The scale ranged from never (1) to always (5). As shown in the above figure, o,n average respondents rated all 10 practices on the survey near the middle of the scale, indicating that the practices were only used sometimes. However, a standardized process for prequalifying suppliers is the most frequently used of the practices. The practice with the lowest adoption rate was use of a C-suite board to help govern risk.
For most organizations, the focus is on tackling IT risk at the tactical level of the supply chain. For example, organizations use supplier evaluations as the primary way of managing risk rather than relying on leadership to help govern IT risk. Organizations also rely on more practical tactics such as adopting an enhanced perimeter defense system to identify IT intrusions rather than the loftier goal of creating a formal registry of IT risks that can then be shared within the enterprise.
In addition to indicating how frequently their organizations use the 10 risk management practices, the survey respondents rated the effectiveness of each from ineffective (1) to highly effective (5). On average, respondents rated all the practices near the middle of the scale, indicating that they regard the practices as somewhat effective. The three most frequently used practices (an enhanced perimeter defense system to detect intrusions, corporate-wide capabilities in cybersecurity and emergency response, and a standardized process for prequalifying suppliers) were also the practices rated most effective.
Although all the practices on APQC’s survey were rated only somewhat effective, these practices are not used regularly by the responding organizations. We suspect that organizations are not seeing excellent results from the practices because they are not using them consistently. More wide-scale adoption of risk management—especially strategic ones—would likely improve the overall performance of supply chain IT risk strategies.





























