During the first quarter of each year, businesses, analysts, journalists and other would-be pundits make their annual predictions. Most are relatively obvious products of trend watching or investment predictions. Very few consider predictions that are more serious in nature, like the ones we'll start to see if Congress doesn't start to implement nation-wide security practices within the pharmaceutical industry.
More than one year after the blood thinner drug Heparin was recalled due to the presence of a tainted ingredient, my prediction is that we will see another incident like this before the year 2010. The FDA has estimated that at least 81 Americans died and hundreds more became sick from severe allergic reactions to the tainted ingredient, which came to light in the early months of 2008. However, we have not seen the last of that scare – in November (nearly one year after the recall) federal marshals had to enter and seize 11 lots of recalled Heparin from Celsus Laboratories, which distributes heparin to drug and medical-device manufacturers both in the United States and internationally.
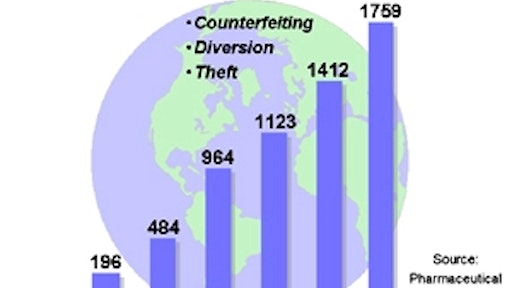
Furthermore, little attention has been turned to the root of the problem, which in this case was that the manufacturers in China intentionally changed the ingredients within the drug in order to cut costs. As economic stresses mount, the frequency of incidents such as these should be expected to rise as the industry comes under increasing pressure to cut costs. Add to this the fact that counterfeiters of legitimate pharmaceuticals enjoy greater profits and face lower risks that do traffickers of illegal drugs and you have an environment where paranoia begets reality – the entire pharmaceutical supply chain can be considered at risk.
While the United States' finished dose drug supply is one of the safest in the world, it is not immune to these concerns, particularly when one includes in the analysis the global drug manufacturing and material sourcing ecosystem. Left unaddressed in a systematic way, product security concerns will lead to a continuance of the patchwork of regulatory mandates that we have today. The result will be an environment that neither provides the level of safety desired nor supports the market access and supply chain efficiencies required to keep drug costs down. It is important for pharmaceutical supply chain participants to take matters into their own hands, analyze the diverse threats they face and build a go-forward plan that not only mitigates product risk but also lays the foundation for better business performance.
The Drug Supply Chain: Global and Under Attack
Global pharmaceutical supply chain control is a challenge without track-and-trace technologies in place. Visibility to one's immediate suppliers and customers is good, yet vision across the entire supply network is nebulous. Once a drug or active ingredient leaves its manufacturer it is left wide open to be adulterated, completely faked, diluted, relabeled, and repackaged or manufactured without authorization. These counterfeit drugs are often physically indistinguishable from the genuine product, but most of the time the counterfeit does not provide the intended therapeutic value. In addition, "legal" drugs manufactured for one market may not meet the efficacy or cGMP quality standards required for distribution in another market.
The lack of visibility and supply chain collaboration leaves the entire legal drug distribution network wide open to the introduction of illegal products, which can occur through the following methods:
- a company illegally participating in drug distribution,
- a seller misrepresenting the true origin of the product, or
- a buyer not verifying the true identity and origin of the product or licensure of the seller.
Together, these form a "drug diversion network."
First, a company can be engaged in criminal activity by selling into the drug distribution network without a license. Pharmacies, clinics, foreign distributors, repackagers and unlicensed wholesalers have been engaged in the illegal sale of drugs to legal entities engaged in drug distribution and dispensation. Very often these individuals change modus operandi by rapidly changing their physical location and through the use of shell companies. These companies are not always the producers of counterfeit products, but they are the crucial vehicle through which illegitimate products are diverted into the legitimate distribution network.
Second, companies both with and without licenses have been caught creating forged documentation in order to portray the sale of legitimate products. The forgeries include invoices, purchase orders, shipping documents and paper pedigrees that purport a legitimate source of the drugs. The legitimate sources being claimed can be either the manufacturer, authorized distributor of record (ADR) or another legal distributor (wholesaler, pharmacy or repackager). The product is sold to an unsuspecting buyer or a buyer that is willing to overlook the procedures required to verify the documentation.
Finally, both companies and individuals within a company have been found to knowingly purchase products from suspicious sources of dubious origin. The lack of licensure and transaction verification combined with limited internal controls enables an individual and/or an organization to accept illegitimate product into the legitimate distribution network.
These three methods combine to create the holes through which large volumes of illegitimate products can flow systemically and undetected into the legitimate distribution network. A counterfeiter seeks to exploit the diversion network in order to sell illegitimate product at volumes and prices that maximize profits. The existence of these kinds of counterfeiting and diversion networks is one reason why the key focus must be on attacking the underlying systemic threats instead of targeting isolated incidents.
Systemic Threats Call for Systemic Protection
When looking at the appropriate response in combating product counterfeiting and drug diversion, it is helpful to assess the underlying threats and proposed tools against the desired outcomes. According to the research carried out at the Massachusetts Institute of Technology (MIT) Auto-ID Lab and elsewhere, there is no single, silver bullet for product security. Serializing products at the item level in order to authenticate product identity at points across the supply network and establishing an ongoing chain of custody through electronic pedigree are a few of the tools that companies can bring to bear on the problem.
Leveraged appropriately, the process visibility, rich data access and operational control of these tools can also provide pharmaceutical companies and their trading partners several benefits including:
- Enhanced flexibility in corporate outsourcing and virtualization programs.
- Improved brand competitiveness and protected brand equity.
- Enhanced sales and operations planning (S&OP) based on channel visibility.
- Optimized reimbursement programs from an efficiency and financial standpoint.
- Lean and responsive manufacturing and distribution operations.
However, which tools to leverage and in what combination often depends on the specific goals of the security program.
Different facets of product security protection may be warranted depending on several dimensions, such as potential patient harm, individual product value, business operational strategy and market brand equity risk. One approach to narrowing down the problem is to focus on the three key foundational goals of pharmaceutical product security – incident investigation, incident detection and threat prevention. Each goal provides a unique set of benefits and mandates a unique set of tools. One way of understanding these goals is to draw analogies from the design of a home security program:
Investigation
If a break-in occurs, how can we facilitate the launch and closure of the investigation into the event? A fingerprint identification process, using unique fingerprint records accessible by a central repository and linked to other information such as individual identity and location, helps police quickly follow up on leads by taking samples from the crime scene.
In the pharma supply chain, investigation can be supported through serialized drug identity tied to a complete, verifiable and non-repudiated chain of custody. This provides legal authorities with extensive and integrated detail on the product, the affected organization and the related financial transactions that can be used to accelerate the investigations of security threats.
Detection
We can raise the bar one step by adding in mechanisms to speed the detection of the break-in. By putting in an alarm system at the house, we gain prompt notification when a security event occurs. This will allow investigators to get on the scene more quickly and start following leads before they get cold.
In the pharma supply chain, we can enhance detection of product security threats in several ways. For example, authentication of serialized product identity and status at point of product receipt can help detect counterfeit or stolen drugs before they are taken into inventory. In addition, mandating receipt of an electronic chain of custody, provided through electronic pedigree, enables the recipient to identify suspicious product movement patterns and detect products that were intended for other geographic regions or supply chain channels.
Prevention
We can further raise the bar by publicly signaling to criminals that this particular house is protected. Publicizing security protections like placing signs on the lawn of the presence of an alarm system will cause thieves to think twice before trying to enter and result in them moving on to potentially easier targets.
In the pharma supply chain, this is accomplished by the public widespread adoption of product security mechanisms such as product serialization, serialized product authentication and electronic pedigree. The result is a security barrier that protects the legitimate ingredient and finished dose supply chain by deterring would-be criminals from seeking simple profits and significantly raising the investment these criminals need to make.
A complete systemic security program would include solutions for all three dimensions. While this is the ultimate goal, its pursuit has to be measured against both the current resources available and the potential business value available from these tools. In addition, a company must decide if it should wait until a regulatory mandate is in place or push forward for other business reasons.
Novis: Protecting Patient Safety with an Eye toward Business Value
One company that decided not to wait until the dust settled is Novis Pharmaceuticals. As discussed earlier in the article, if you want to prevent a Heparin-like incident and at the same time open the doors to new business value opportunities, the next step is to beat legislation and start securing your supply chain now. Novis Pharmaceuticals, a leading distributor of biotherapeutic products to healthcare providers, didn't wait for legislation to move forward with a Patient Safety Initiative Program. In September 2007, Novis launched the initial Program phase to strengthen product security using electronic pedigrees for all the products it handles, starting with high-risk drugs like Heparin and ones that provide its customers the most value.
Product serialization was also a key part of the equation for Novis, yet the industry wasn't ready to take this next step en masse. So, Novis has also taken the proactive step of blending the SupplyScape Nexus/E-Pedigree platform with an internal serialization solution based on SAP AG solutions to further product tracking throughout the supply chain. This newly launched inventory tracking system, NOVIS RxID, is set to protect product integrity through a systemic product security program incorporating both item-level serialization and electronic pedigree. Particular attention was also given on how these security elements would be extended to Novis' customers.
Underlying the design of their product security program was Novis' ability to leverage these investments for business value. All aspects of the business were examined for opportunities, including internal operational processes and external trade relationships. First, Novis is leveraging the data access and process visibility of the SaaS-based Nexus environment to drive internal operational efficiencies. Novis distributes pharmaceuticals from five regional distribution facilities based in the United States and Puerto Rico. Each of these facilities manages a variety of processes, including initial distribution, returns processing and recall management. The integrated Novis/SupplyScape system provides a new level of control and decision-making across the business.
With Novis' forward-thinking program, differentiated customer service was also a goal. With the new system in place, customers can also more easily access information about their drugs – something the competition cannot claim. Novis' system is expected to provide a Web-based portal to enable customers to view and manage their drug supply and related pedigree information through their entire process. This eliminates the necessity of customers procuring their own extensive product security systems. Additional value-add is provided by the ability to develop event management functionality that can alert customers based on predefined business rules. For example, alerts can be sent prior to a drug reaching its expiration date or if a drug, needing refrigeration, is not scanned into its proper storage location.
With an official launch of its NOVIS RxID program slated for mid-2009, Novis will become one of the leaders in demonstrating that protecting patient safety can be good business if you keep your eye on your key strategic imperatives, be they product integrity, operational efficiency, customer service, or other.
Conclusion
As recent incidents making headlines and historical issues make clear, threats to pharmaceutical product security aren't going away. Indeed, the trend is an increasing one and current economic conditions will only serve to stimulate this trend. The underlying regulatory environment, both in the United States and in other regions such as the European Union, does not appear to be converging on any one formula. In addition, no single security element appears to provide the systemic security protections needed at reasonable economic cost. The question for many businesses in this uncertain environment is whether to sit back and wait for clarity or move forward and drive the bus. Early evidence suggests that those firms that seize the opportunity by starting now with detailed strategic analysis and business planning which incorporates all facets of the business will be best positioned to not only survive but thrive. The question is where your business lies on this spectrum of readiness?


























